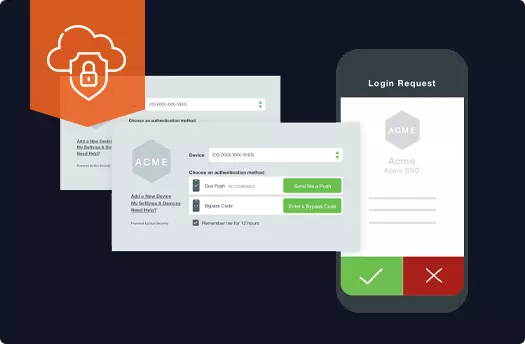
What are the Factors of Authentication?
Factors are the pieces of information a user can provide to verify their identity. 2FA is the most commonly used, but there are, in fact, five factors of authentication used by security professionals today.
Knowledge Factor
The knowledge factor verifies identity by requesting information only an individual user would know. The most common example of a knowledge factor of authentication is a password. A user’s password should be private only to them, allowing them to use it as a method to confirm their identity.
Possession Factor
Possession factors verify the identity of a user by requiring proof of information that only the user should possess. Tokens are a commonly used possession factor of authentication. These tokens generate a rotating passcode that users must physically carry on their person.
Duo Mobile combines the knowledge factor and possession factor of authentication to create the world’s most trusted 2FA platform. Two other possession factors of authentication are HMAC-based One-Time Password (HOTP) and Time-based One-time Password (TOTP). Both authentication methods generate temporary passwords from a physical device carried by the user. HOTP tokens expire once they are used while TOTP tokens expire if not used within thirty seconds.
Inherence Factor
Inherence factors of authentication verify the identity of a user by using attributes that would belong only to that user. Fingerprint scanning is the most obvious inherence factor used today.
Fingerprints are unique to individuals, so many organizations use them as a way to confirm who their users are. In addition to fingerprints, there are many other inherence factors used today: voice, handprints, face recognition, and more.
Location Factor
Location factors of authentication confirm the identity of a user based on their location in the world. If a user had registered an account in one country, for example, and suddenly there are login attempts from another, location factors could trigger and attempt to verify the identity of the new user. Many location factors are based on the IP address of the original user and compares the address to that of the new attempt to access information.
Time Factor
Time factors of authentication verify the identity of a user by challenging the time of the access attempt. This is based on the assumption that certain behaviors (like logging into a work computer) should happen within predictable time ranges. If an attempt to access a platform happens outside of the usual time range, the attempt can be challenged or terminated until a user can verify their identity.